Former Director of National Intelligence (DNI) James Clapper was always a doofus, sticking his foot in his mouth about all kinds of Intelligence Community stuff. It was his doofusness that led to President Obama keeping him as DNI, while the rest of the IC worked around him (a little funny at the time).
Former Director of National Intelligence (DNI) James Clapper was always a doofus, sticking his foot in his mouth about all kinds of Intelligence Community stuff. It was his doofusness that led to President Obama keeping him as DNI, while the rest of the IC worked around him (a little funny at the time).
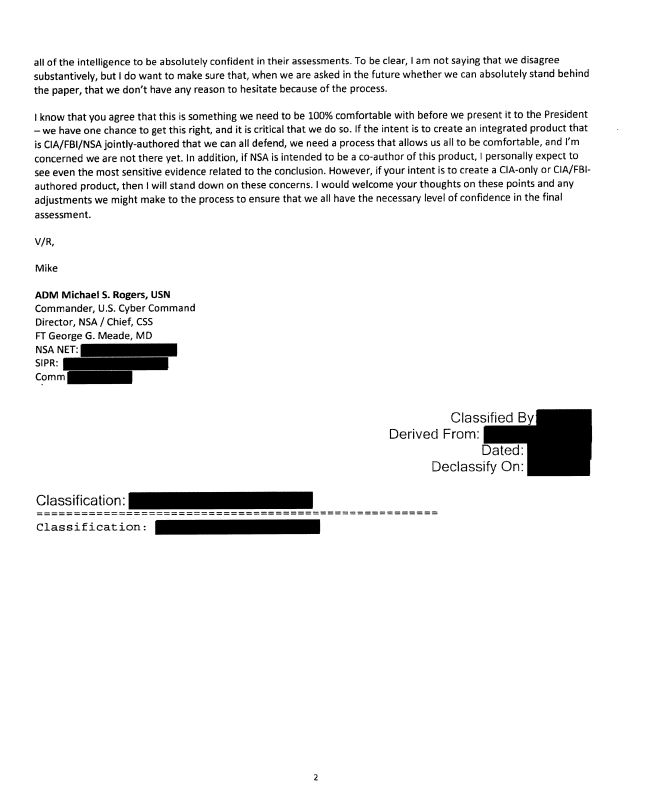
Today, current Director of National Intelligence, Tulsi Gabbard, declassified and released the content of an email exchange between then NSA Director Mike Rogers and DNI Clapper about the bogus nature of the rushed December 2016 Intelligence Community Assessment, that Obama wanted to help frame the Trump-Russia story.
Adm Mike Rogers is telling James Clapper his NSA team was not comfy with manufacturing and spinning intelligence for a political hit job on the incoming administration. Clapper responds to Rogers telling him to get on board, because this level of IC fabrication requires all key elements to be on the same page. Clapper saying the Russian stuff, “is our story, and we’re sticking to it.”
As noted by Tulsi Gabbard: “Newly declassified Top Secret emails sent on December 22, 2016 complying with President Obama’s order to create the manufactured January 2017 ICA about Russia expose how DNI James Clapper demanded the IC fall in line behind the Russia Hoax. Clapper admits that it was a “team sport” that required “compromise on our ‘normal modalities'”.
This release by DNI Tulsi Gabbard is a solid drop of evidence, albeit in hindsight.
In real time in 2016 and 2017, CTH was watching Adm Mike Rogers very closely, because we could tell he was not a willing participant in the overall fraud. In fact, the pressure on him was transparently obvious to anyone paying attention and listening to the actual words from NSA Director Rogers at the time.
It is not coincidental the two most politicized intelligence operatives, John Brennan (CIA) and James Comey (FBI), presented the information along with like-minded political traveler ODNI James Clapper. While Admiral Mike Rogers (NSA) is also included in the report authorship, it is largely overlooked that Rogers only held a “moderate confidence” in the overall report finding. It was only Brennan and Comey who claimed “high confidence” in the overall report content.
We have continually pointed out at the time the report was written it appeared to be entirely political in construct. The intent of the report was to provide source material for the overall Russian conspiracy narrative; and also establish some framework for the White House to take action, vis-a-vis sanctions.
Against the backdrop of the December 2016 sanctions announcement, President Obama’s administration released the Joint Analysis Report claiming it outlined details of Russia’s involvement hacking into targeted political data-base or computer systems during the election.
Except it didn’t
Not even a little.
 The “Russian Malicious Cyber Activity – Joint Analysis Report” (full pdf below) was/is pure nonsense. It outlines nothing more than vague and disingenuous typical hacking activity that is no more substantive than any other hacking report on any other foreign actor.
The “Russian Malicious Cyber Activity – Joint Analysis Report” (full pdf below) was/is pure nonsense. It outlines nothing more than vague and disingenuous typical hacking activity that is no more substantive than any other hacking report on any other foreign actor.
This might as well be a report blaming Nigerian fraud phone solicitors for targeting U.S. phone numbers. Just because you didn’t actually win the Nigerian national lottery doesn’t mean the Nigerian government are targeting you for your portion of the lottery revenue.
The December FBI report was/is, well, quite simply, pure horse-pucky.
What the report does well is using ridiculous technical terminology to describe innocuous common activity. Example: “ATPT29” is Olaf, the round faced chubby guy probably working from his kitchen table; and “ATPT28” is his unemployed socially isolated buddy living in Mom’s basement down the street.
This paragraph below is priceless in it’s humorous and disingenuous gobblespeak:
Both groups have historically targeted government organizations, think tanks, universities, and corporations around the world. APT29 has been observed crafting targeted spearphishing campaigns leveraging web links to a malicious dropper; once executed, the code delivers Remote Access Tools (RATs) and evades detection using a range of techniques.
APT28 is known for leveraging domains that closely mimic those of targeted organizations and tricking potential victims into entering legitimate credentials. APT28 actors relied heavily on shortened URLs in their spearphishing email campaigns. Once APT28 and APT29 have access to victims, both groups exfiltrate and analyze information to gain intelligence value.
These groups use this information to craft highly targeted spearphishing campaigns. These actors set up operational infrastructure to obfuscate their source infrastructure, host domains and malware for targeting organizations, establish command and control nodes, and harvest credentials and other valuable information from their targets.
(*note the emphasis I placed in the quote) All that nonsense is saying is a general explanation for how hacking, any hacking, is generally carried out. The entire FBI report was nothing more than a generalized, albeit techno-worded, explanation for how Nigerians, Indians, or in this case Russians, attempt to gain your email passwords etc., nothing more.
[scribd id=335307016 key=key-qvjYK3gLD9WdgOskmgoe mode=scroll]
What was alarming to consider was: A) how far the various radical leftists were willing to go to create a straw man crisis for political benefit; and B) how diminished the executive office of the U.S. presidency actually became amid this level of ridiculous propaganda.
There’s no doubt the intended outcome was to create internal confusion amid the U.S. electorate, and seed a media narrative. There were/are millions of people who bought into these widely discussed fabrications.
Consider the example inside a Yahoo News article showcasing the report:
[…] The US intelligence community has concluded that a hack-and-release of Democratic Party and Clinton staff emails was designed to put Trump — a political neophyte who has praised Putin — into the Oval Office. (link)
There was no evidence the DNC was “hacked” (WikiLeaks claims the information was an inside job of “leaking”), Hillary Clinton blames the Macedonians, and even John Podesta admitted himself he was a victim of an ordinary “phishing” password change scam. Not exactly a “hack” per se’.
Does hacking exist, of course it does. Do hackers exist in every country connected by the internet, of course they do. Do state governments participate in hacking offense and defense, again – yes, of course they do. And yes, the FBI and U.S. intelligence community act purposefully against all participants they can catch.
But what does that intellectual truism have to do with the specific allegation that hostile Russian hackers attempted to gain entry into the DNC or John Podesta? These are two entirely different issues which the Obama administration (Brennan and Comey) attempted to conflate simply for political and ideological purposes.
Here is where we see the overall intended and conflated outcome. Consider the Yaho0 media paragraph above against the headline which accompanied the content:
There’s a reasonable case to be made that all of those previous political players have quite a bit to hide within the construct of the entire narrative. Some like James Comey, and possibly Susan Rice, appear to have violated laws on leaking information and unmasking U.S. citizens within intelligence reports.
Former CIA Director John Brennan has clearly established his own exit from the risk matrix. While former ODNI James Clapper is almost too inept to be held accountable for any of it.
It would be disingenuous in the extreme to ignore that NSA Director Mike Rogers was the least willing and least engaged intelligence leader within the scheme and simultaneously highly political ODNI James Clapper was calling for him to be fired.
Admiral Mike Rogers traveled to Trump Tower (after the election) on November 17th without notifying the White House or Clapper. The next day, November 18th, President-Elect Trump moved the entire Transition Team to his New Jersey country club. Mike Rogers remains the current head of the NSA.